Installing LMDE6 with full disk encryption using RAID, LUKS, LVM2 and USB unlock on a computer with a UEFI bootloader

by Semyon A Mironov, 5/2025
This document describes the creation of the following scheme
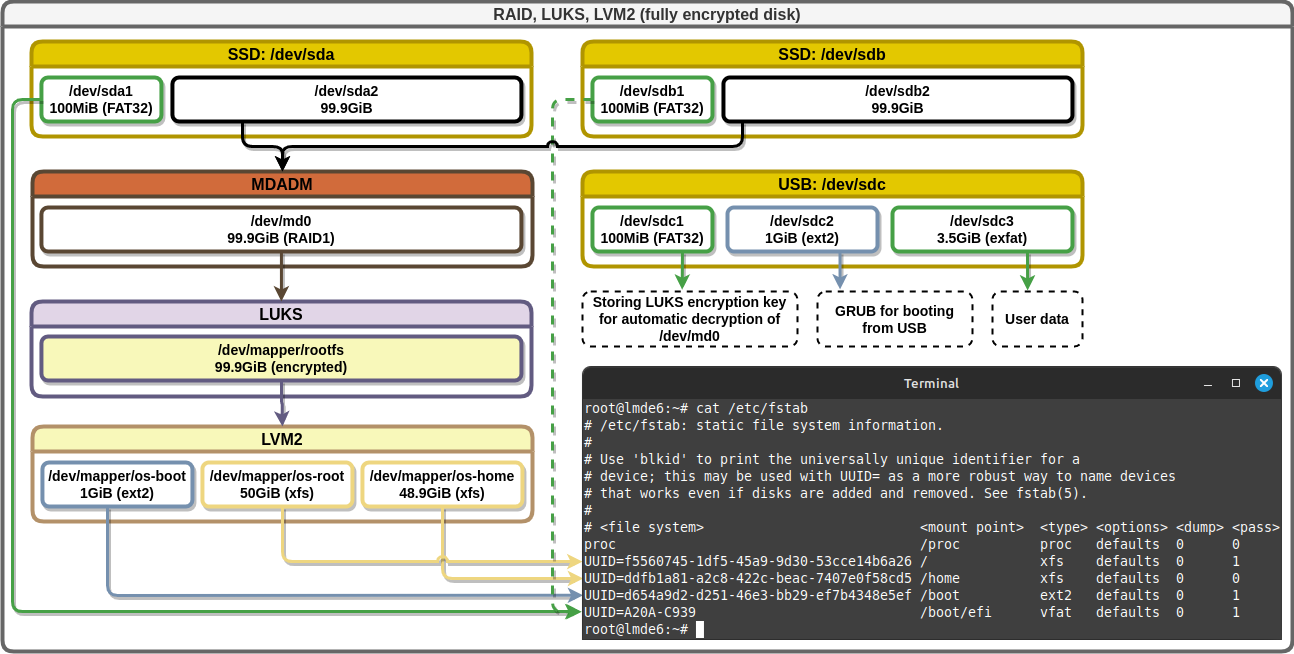
Table of Contents
- Booting from a LIVE-iso
- Preparing a LIVE system
- Preparing the disks
- Installing the LMDE operating system
- Configuring the LMDE operating system
- Entering the system
- Configuring locale
- Configuring time
- Configuring keyboard
- Editing the
/etc/hostnamefile - Editing the
/etc/hostsfile - Editing the
/etc/fstabfile - Set the root user password
- Creating a user
- Configuring LUKS with password unlock
- Configuring LUKS with USB unlock
- Update list of available packages
- Configuring MDADM
- Generate an initramfs image
- Configuring GRUB
- Cloning of the
EFIpartition fromSDAonSDB - Edit the
EFIboot menu - Removing packages
- Reboot the machine
- Useful links
Booting from a LIVE-iso
Select booting from a USB/CD image
Select "Start LMDE 6 64-bit"
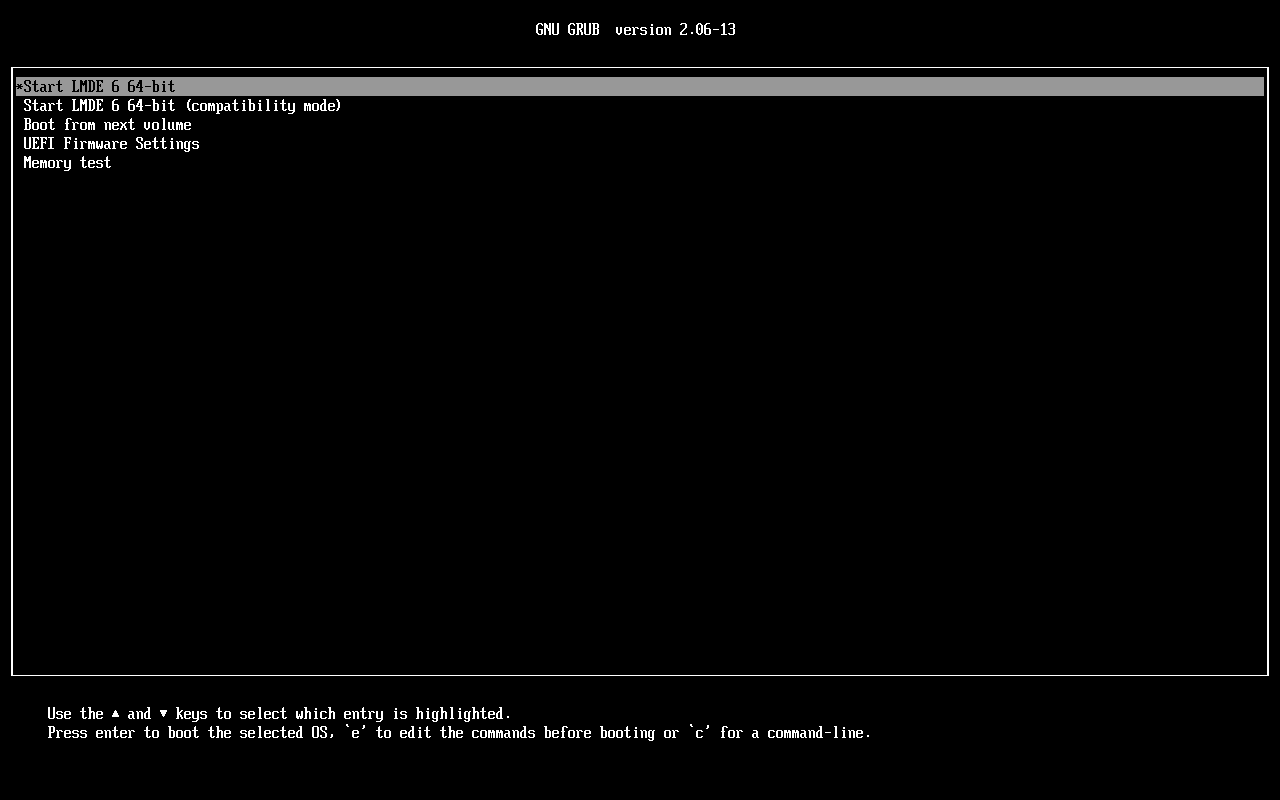
Press e to edit the commands before booting
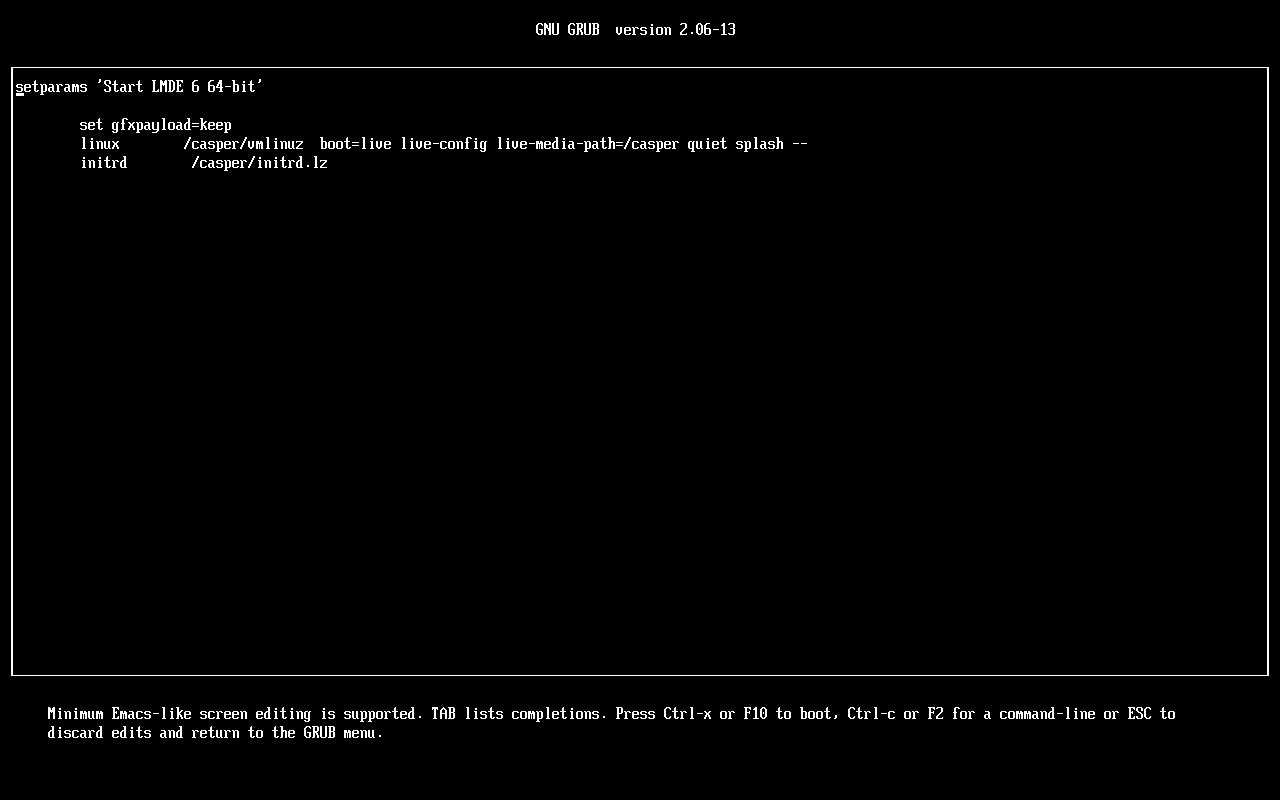
Add the nomodeset parameter and press F10 to boot
The kernel’s command-line parameters
LMDE 6 Desktop live

Preparing a LIVE system
Open the terminal

Switch to the root user
sudo 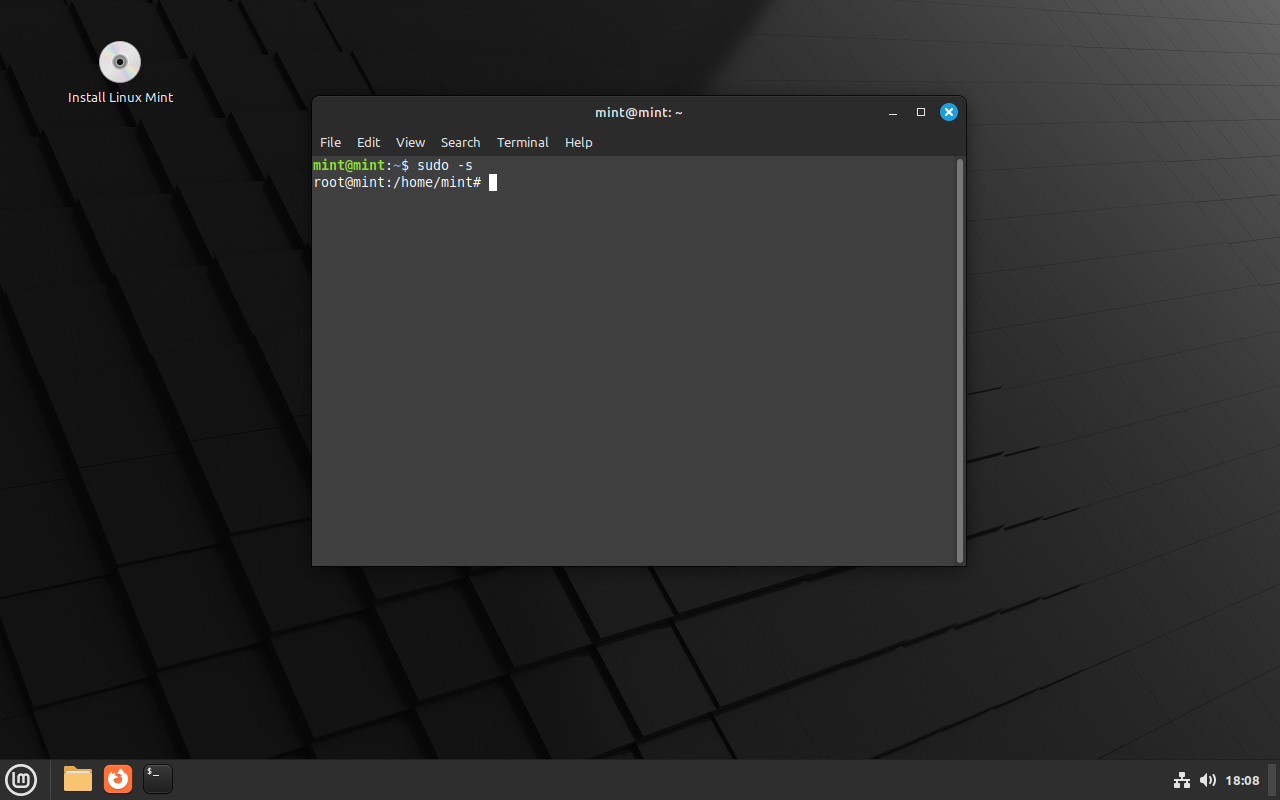
Change the host name
export HOST_NAME="lmde" # set a variable with a new host name for the operating system to install
hostname "$HOST_NAME" # change the host nameCheck
hostnameTime setup in a LIVE system
dpkg-reconfigure tzdataPreparing the disks
Creating partitions
List information about block devices
lsblk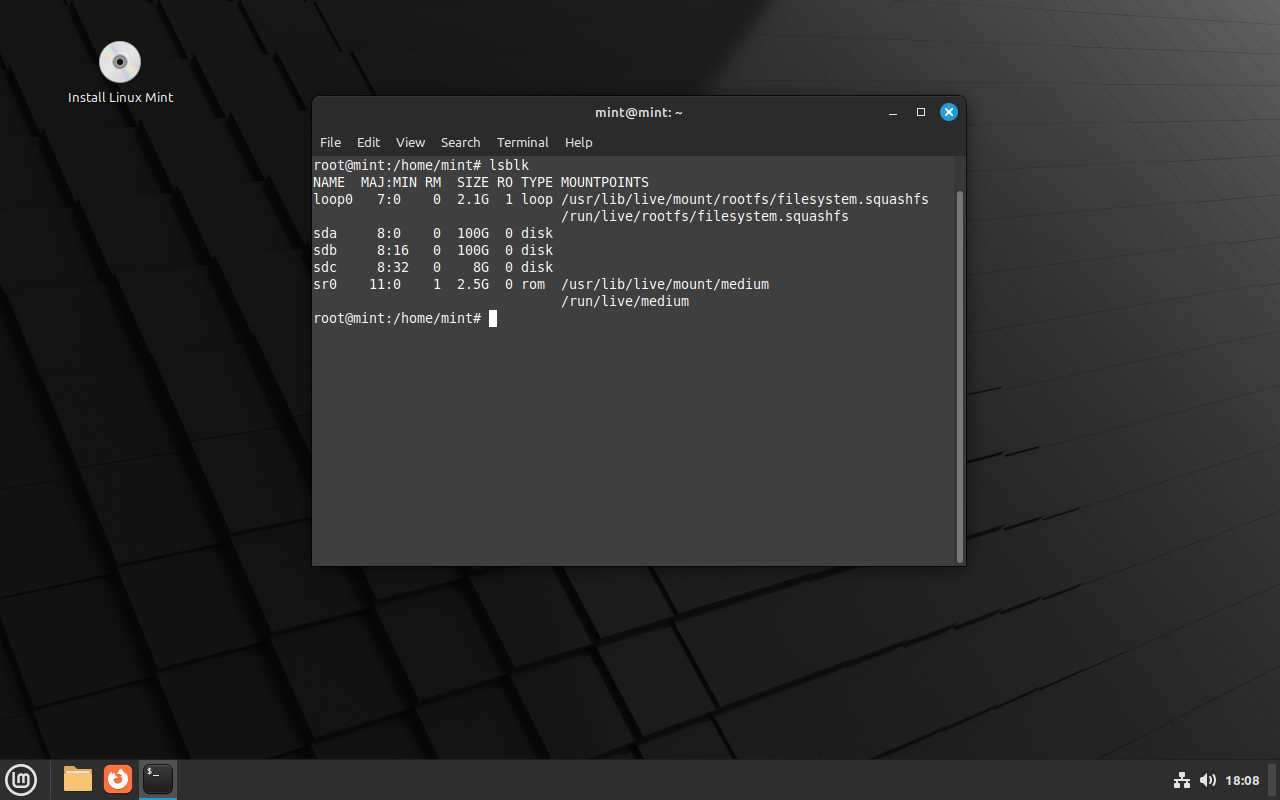
Save the disk names to variables
SDA="/dev/sda"
SDB="/dev/sdb"Creating two partitions on SDA for EFI and mirror array
Run the
fdiskprogram for theSDAdisk:fdisk "${SDA:-/dev/sda}"Create partitions on the disk by following the following list of commands:
m # print help p # print the partition table g # create a new empty GPT partition table n # add a new partition No.1 1 # partition number # first sector (2048) +100M # last sector p # print the partition table n # add a new partition No.2 2 # partition number # first sector (206848) # last sector p # print the partition table l # list known partition types q # quit from list known partition types t # change a partition type No.1 1 # partition number 1 # EFI System t # change a partition type No.2 2 # partition number 42 # Linux RAID p # print the partition table x # extra functionality (experts only) m # print help (for GPT) n # change partition name No.1 1 # partition number EFI # new name No.1 n # change partition name No.2 2 # partition number RAID1 # new name No.2 p # print the partition table r # return to main menu p # print the partition table w # write table to disk and exit
Creating two partitions on SDB for EFI and mirror array
cat << FDISK | fdisk "${SDB:-/dev/sdb}"
g # create a new empty GPT partition table
n # add a new partition No.1
1
+100M
p # print the partition table
n # add a new partition No.2
2
p # print the partition table
t # change a partition type No.1
1
1
t # change a partition type No.2
2
42
p # print the partition table
x # extra functionality (experts only)
n # change partition name No.1
1
EFI
n # change partition name No.2
2
RAID1
p # print the partition table
r # return to main menu
p # print the partition table
w # write table to disk and exit
FDISKComments are allowed only when calling commands Spaces at the beginning and end of commands and values are ignored
Creating a mirror array with MDADM
MDADM - Multiple Disk and Device Management
Download lists of new packages
apt updateInstalling the mdadm package on a LIVE system
apt install mdadmCreating a mirror array /dev/md0
mdadm /dev/md0 1 2 "${SDA:-/dev/sda}2" "${SDB:-/dev/sdb}2"Checking the RAID array status
watch =1 cat /proc/mdstatAdditional commands for MDADM
Show help
mdadmDisplay details of an array
mdadm | grep '^ARRAY'Save the array configuration
nano /etc/mdadm/mdadm.confStop the array
mdadm /dev/md0Assemble a previously created array
mdadmHotadd subsequent devices to the array
mdadm /dev/md0 /dev/sdc2Subsequent devices are re-added
mdadm /dev/md0 /dev/sde2Delete super-blocks on the disks from which the array is assembled
mdadm /dev/sda2 /dev/sde2
RAID encryption with LUKS
LUKS - Linux Unified Key Setup
Encrypting /dev/md0
cryptsetup luksFormat pbkdf2 /dev/md0Unlocking /dev/md0 to /dev/mapper/rootfs
This command unlocks /dev/md0 on /dev/mapper/rootfs
cryptsetup luksOpen /dev/md0 rootfsAdditional commands for LUKS
Show help
cryptsetupClose device (remove mapping)
cryptsetup close /dev/mapper/rootfsShow device status
cryptsetup status /dev/mapper/rootfsDump LUKS partition information
cryptsetup luksDump /dev/md0Add key to LUKS device
cryptsetup luksAddKey /dev/md0 [<new key file>]Changes supplied key or key file of LUKS device
cryptsetup luksChangeKey /dev/md0 <key slot>Removes supplied key or key file from LUKS device
cryptsetup luksRemoveKey /dev/md0 [<new key file>]Wipes key with number
<key slot>from LUKS devicecryptsetup luksKillSlot /dev/md0 <key slot>
Creating LVM
LVM - Logical volume manager
Initializing /dev/mapper/rootfs to use LVM
pvcreate /dev/mapper/rootfsDisplay various attributes of physical volume(s)
pvdisplayor display information about physical volumes
pvs
Creating a volume group os on /dev/mapper/rootfs
vgcreate os /dev/mapper/rootfsDisplay volume group information
vgdisplayor display information about volume groups
vgdisplay
Creating the boot logical volume
lvcreate 1G boot osCreating the root logical volume
lvcreate 50G root osCreating the home logical volume
lvcreate 100%FREE home osDisplay information about a logical volume
lvdisplayor display information about logical volumes
lvs
Additional commands for LVM
Deactivation/activation LVM
Deactivating Volume Groups:
vgchange n osActivating Volume Groups:
vgchange y osRename LVM
Rename a logical volume:
lvrename os root linuxor:
lvrename /dev/os/root linuxRename a volume group:
vgrename os sysRemove LVM
Remove logical volume(s):
lvremove /dev/os/boot lvremove /dev/os/root lvremove /dev/os/homeor remove all logical volumes in the volume group:
lvremove osRemove volume group(s):
vgremove osRemove LVM label(s) from physical volume(s):
pvremove /dev/mapper/rootfs
Creating a file systems
Format the
EFIpartition:mkfs.fat 32 EFI "${SDA:-/dev/sda}1"/dev/sdb1 - do not format
Format the
bootpartition:mkfs.ext2 boot /dev/mapper/os-bootFormat the
rootpartition:mkfs.xfs root /dev/mapper/os-rootFormat the
homepartition:mkfs.xfs home /dev/mapper/os-homeAdditional commands for mkfs
Remove a file system
dd if=/dev/zero of=/dev/sda1 bs=512 count=1 conv=notrunc
Installing the LMDE operating system
Mounting ISO image
Create a directory for mounting ISO image:
mkdir /sourceMount the ISO image:
mount loop squashfs /run/live/medium/live/filesystem.squashfs /source
Mounting root partition
Create a directory to mount the
rootpartition of the future LMDE operating system:mkdir /targetMount the root (
/) partition:mount /dev/mapper/os-root /targetCreate directories to mount the
bootandhomepartitions:mkdir /target/{boot,home}Mount the
homepartition:mount /dev/mapper/os-home /target/homeMount the
bootpartition:mount /dev/mapper/os-boot /target/bootCreate a directory to mount the
EFIpartition:mkdir /target/boot/efiMount the
EFIpartition:mount "${SDA:-/dev/sda}1" /target/boot/efi
Copying system files

Copy the operating system files from the ISO image to the root partition:
rsync /source/ /target/Copy the local domain name system configuration file:
cp /etc/resolv.conf /target/etc/Check
cat /target/etc/resolv.conf
Unmount ISO image
umount /sourceConfiguring the LMDE operating system
Entering the system
Mount the system directories of the LIVE system to the
rootpartition of the future LMDE operating system:for FS in /proc /run /tmp /sys /sys/firmware/efi/efivars /dev /dev/shm /dev/pts do mount "$FS" "/target$FS" done--bind- mount a subtree somewhere elseMake
/targetthe root directory:chroot /target
Configuring locale
dpkg-reconfigure localescat <<LOCALE > /etc/default/locale
# File generated by update-locale
LC_CTYPE="en_US.UTF-8"
LC_ALL="en_US.UTF-8"
LANG="en_US.UTF-8"
LANGUAGE="en_US:en"
LOCALECheck
cat /etc/default/localeConfiguring time
dpkg-reconfigure tzdataConfiguring keyboard
dpkg-reconfigure keyboard-configurationEditing the /etc/hostname file
echo "${HOST_NAME:-lmde}" > /etc/hostnameCheck
cat /etc/hostnameEditing the /etc/hosts file
Save a text file that contains a database of domain names and is used when translating them to network host addresses
cat <<HOSTS > /etc/hosts
127.0.0.1 localhost
127.0.1.1 ${HOST_NAME:-lmde}
# The following lines are desirable for IPv6 capable hosts
::1 ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
ff02::3 ip6-allhosts
HOSTSCheck
cat /etc/hostsEditing the /etc/fstab file
Get UUID of the system partitions:
EFI_UUID="$(blkid UUID value "${SDA:-/dev/sda}1")" BOOT_UUID="$(blkid UUID value /dev/mapper/os-boot)" ROOT_UUID="$(blkid UUID value /dev/mapper/os-root)" HOME_UUID="$(blkid UUID value /dev/mapper/os-home)"Check
echo " EFI_UUID: $EFI_UUID" echo "BOOT_UUID: $BOOT_UUID" echo "ROOT_UUID: $ROOT_UUID" echo "HOME_UUID: $HOME_UUID"Save the mounting points of the system partitions:
cat <<FSTAB > /etc/fstab # /etc/fstab: static file system information. # # Use 'blkid' to print the universally unique identifier for a # device; this may be used with UUID= as a more robust way to name devices # that works even if disks are added and removed. See fstab(5). # # <file system> <mount point> <type> <options> <dump> <pass> proc /proc proc defaults 0 0 UUID=$ROOT_UUID / xfs defaults 0 1 UUID=$HOME_UUID /home xfs defaults 0 0 UUID=$BOOT_UUID /boot ext2 defaults 0 1 UUID=$EFI_UUID /boot/efi vfat defaults 0 1 FSTABCheck
cat /etc/fstab
Set the root user password
passwd rootCreating a user
Set variables for use in subsequent commands:
USER_NAME="sam" # name of the user to be created FULL_NAME="Semyon A Mironov" # full name of the user to be createdCreate a user:
useradd ${FULL_NAME:+ "$FULL_NAME"} /bin/bash adm,audio,bluetooth,cdrom,dialout,dip,fax,floppy,lpadmin,netdev,plugdev,scanner,sudo,tape,users,video "$USER_NAME"
Delete a user
deluser "$USER_NAME"Set user passwords:
passwd "$USER_NAME"
Configuring LUKS with password unlock
Editing the /etc/crypttab file
Get UUID of LUKS device:
LUKS_UUID="$(cryptsetup luksUUID /dev/md0)"Check
echo "LUKS_UUID: $LUKS_UUID"Save configuration for encrypted block devices:
cat <<CRYPTTAB > /etc/crypttab # <target name> <source device> <key file> <options> rootfs UUID=$LUKS_UUID none luks,discard CRYPTTABCheck
cat /etc/crypttab
Configuring LUKS with USB unlock
Creating three partitions on a USB drive for EFI, boot and user data
Insert the USB drive into the host and define it in the
lsblkoutputSet variables for use in subsequent commands:
USB_DRIVE="/dev/sdc" # USB drive from the `lsblk` output USB_DRIVE_MOUNT_POINT="/media" # Specify an existing empty directory for connecting the USB drive CRYPTTAB_KEY="my_key.lek" # Name of the key file to create on the USB drive LUKS_SCRIPT="/bin/luksunlockusb" # Name and path to the script to unlock using CRYPTTAB_KEYCheck
echo " USB_DRIVE: ${USB_DRIVE:-/dev/sdc}" echo "USB_DRIVE_MOUNT_POINT: $USB_DRIVE_MOUNT_POINT" echo " CRYPTTAB_KEY: $CRYPTTAB_KEY" echo " LUKS_SCRIPT: $LUKS_SCRIPT"Creat partitions on USB drive:
cat << FDISK | fdisk "${USB_DRIVE:-/dev/sdc}" g # create a new empty GPT partition table n # add a new partition No.1 1 +100M p # print the partition table n # add a new partition No.2 2 +1G p # print the partition table n # add a new partition No.3 3 p # print the partition table t # change a partition type No.1 1 1 p # print the partition table x # extra functionality (experts only) n # change partition name No.1 1 EFIUSB p # print the partition table n # change partition name No.2 2 BOOTUSB p # print the partition table n # change partition name No.3 3 USB p # print the partition table r # return to main menu p # print the partition table w # write table to disk and exit FDISK
Creating a file systems on USB drive
Format the
EFIUSBpartition:mkfs.fat EFIUSB "${USB_DRIVE:-/dev/sdc}1"Format the
BOOTUSBpartition:mkfs.ext2 BOOTUSB "${USB_DRIVE:-/dev/sdc}2"Format the
USBpartition:mkfs.exfat USB "${USB_DRIVE:-/dev/sdc}3"
Mounting USB drive
Mount the
BOOTUSBpartition:mount "${USB_DRIVE:-/dev/sdc}2" "$USB_DRIVE_MOUNT_POINT"Create a directory to mount the
EFIUSBpartition:mkdir "$USB_DRIVE_MOUNT_POINT/efi"Mount the
EFIUSBpartition:mount "${USB_DRIVE:-/dev/sdc}1" "$USB_DRIVE_MOUNT_POINT/efi"
Creating LUKS encryption key
Change the shell working directory:
cd "$USB_DRIVE_MOUNT_POINT/efi" pwdCreate a 256 byte key file with random data (.lek = LUKS Encryption Key):
dd if=/dev/urandom bs=1 count=256 > "$CRYPTTAB_KEY"The contents of the key file can be anything, for example, a photo
Add key to LUKS device:
cryptsetup luksAddKey /dev/md0 "$CRYPTTAB_KEY"Go back to the previous directory:
cd - pwd
Creating a script to search for the LUKS encryption key
Get UUID of LUKS device:
LUKS_UUID="$(cryptsetup luksUUID /dev/md0)"Check
echo "LUKS_UUID: $LUKS_UUID"Create a script that will search for the key on USB drive during boot
Script for any USB drive
cat <<SCRIPT > "$LUKS_SCRIPT" #!/bin/sh sleep 3 test -d /mnt || { test ! -e /mnt && mkdir /mnt 2>/dev/null } && for USB_UUID in /dev/disk/by-uuid/* do if mount "\$USB_UUID" /mnt then for CRYPTTAB_KEY_FILE in "\$CRYPTTAB_KEY" "\$CRYPTTAB_KEY.lek" do test -f "/mnt/\$CRYPTTAB_KEY_FILE" || continue cat "/mnt/\$CRYPTTAB_KEY_FILE" || break umount /mnt || : exit done umount /mnt || : fi done 2>/dev/null || : # Please comment out this line if you don't want to ask for a password /lib/cryptsetup/askpass "Please unlock disk (\$CRYPTTAB_NAME): " SCRIPTCheck
cat "$LUKS_SCRIPT"Script for one specific USB drive
Get UUID of USB device:
USB_UUID="$(blkid UUID value "${USB_DRIVE}1")"Check
echo "USB_UUID: $USB_UUID"Save script:
cat <<SCRIPT > "$LUKS_SCRIPT" #!/bin/sh sleep 3 test -e "/dev/disk/by-uuid/$USB_UUID" && { test -d /mnt || { test ! -e /mnt && mkdir /mnt } && mount "/dev/disk/by-uuid/$USB_UUID" /mnt && { for CRYPTTAB_KEY_FILE in "\$CRYPTTAB_KEY" "\$CRYPTTAB_KEY.lek" do test -f "/mnt/\$CRYPTTAB_KEY_FILE" || continue cat "/mnt/\$CRYPTTAB_KEY_FILE" || break umount /mnt || : exit done umount /mnt || : } } 2>/dev/null || : # Please comment out this line if you don't want to ask for a password /lib/cryptsetup/askpass "Please unlock disk (\$CRYPTTAB_NAME): " SCRIPTCheck
cat "$LUKS_SCRIPT"
WARNING: If you decide to comment out the password request string in the script, then make sure to perform a pre-test using a key from a USB storage device. Otherwise, you will lose access to the encrypted data.
Make the script executable:
chmod u+rwx,go+rx "$LUKS_SCRIPT"
Editing the /etc/crypttab file to use a script
cat <<CRYPTTAB > /etc/crypttab
# <target name> <source device> <key file> <options>
rootfs UUID=$LUKS_UUID $CRYPTTAB_KEY luks,discard,keyscript=/bin/luksunlockusb
CRYPTTABCheck
cat /etc/crypttabUpdate list of available packages
apt updateConfiguring MDADM
Installing the mdadm package
apt install mdadmSaving the array configuration
Display details of an array:
ARRAY="$(mdadm | grep '^ARRAY')"Check
echo "$ARRAY"Save the array configuration:
sed "s|^ARRAY.*$|$ARRAY|" /etc/mdadm/mdadm.confCheck
cat /etc/mdadm/mdadm.conf
Generate an initramfs image
If you follow the steps in Configuring LUKS with USB unlock, add some initramfs modules:
cat << MODULES >> /etc/initramfs-tools/modules vfat nls_cp437 nls_ascii usb_storage libblkid MODULESCheck
cat /etc/initramfs-tools/modulesCreating
/boot/initrd.img-*:/usr/sbin/update-initramfs.orig.initramfs-tools all
Configuring GRUB
Installing the grub package
apt install grub-efiConfigure grub to use a encrypted disk
echo 'GRUB_ENABLE_CRYPTODISK=y' >> /etc/default/grubInstalling grup on SDA
grub-install =en@quot "${SDA:-/dev/sda}"Update grub
Re create a grub config file based on your disk partitioning schema
update-grubInstalling grup on USB drive
Follow this step if you have completed the steps described in step Configuring LUKS with USB unlock
Creating the
grub/fonts/directory on a USB drive:mkdir "$USB_DRIVE_MOUNT_POINT/grub/fonts/"Copying the
UbuntuMono16.pf2font to USB drive:cp /boot/grub/fonts/UbuntuMono16.pf2 "$USB_DRIVE_MOUNT_POINT/grub/fonts/"Umount the
EFIpartition:umount "${SDA:-/dev/sda}1"Umount the
bootpartition:umount /dev/mapper/os-bootUmount the
EFIUSBpartition:umount "${USB_DRIVE:-/dev/sdc}1"Umount the
BOOTUSBpartition:umount "${USB_DRIVE:-/dev/sdc}2"Mount the
BOOTUSBpartition:mount "${USB_DRIVE:-/dev/sdc}2" /bootMount the
EFIUSBpartition:mount "${USB_DRIVE:-/dev/sdc}1" "/boot/efi"Installing
grupon USB drive:grub-install =en@quot "${USB_DRIVE:-/dev/sdc}"Update
grubon USB drive:update-grub
Cloning of the EFI partition from SDA on SDB
dd if="${SDA:-/dev/sda}1" of="${SDB:-/dev/sdb}1" bs=64K status=progressEdit the EFI boot menu
Print additional information:
efibootmgrDelete bootnum:
efibootmgr 00000000 - bootloader number
Remove all unnecessary bootloaders
Add bootorder from a USB drive:
Follow this step if you have completed the steps described in step Configuring LUKS with USB unlock
efibootmgr "${USB_DRIVE:-/dev/sdc}" 1 "usbkey" /EFI/debian/shimx64.efiNote: option
"usbkey", where"usbkey"is an arbitrary bootloader nameAdd bootorder from a SDA and SDB drives:
efibootmgr "${SDA:-/dev/sda}" 1 "Disk1" /EFI/debian/shimx64.efi efibootmgr "${SDB:-/dev/sdb}" 1 "Disk2" /EFI/debian/shimx64.efiNote: option
"Disk1", where"Disk1"is an arbitrary bootloader name
Removing packages
Remove packages and their system-wide configuration files
apt purge live-config* live-installer* live-boot* live-tools*Reboot the machine
Exit the
chrootenvironment:exitReboot the machine:
shutdown now
Useful links
Installing LMDE to nvme mdadm raid
update-initramfs is disabled (live system is running without media mounted on /run/live/medium)
Using A Live CD/USB To Fix Your Current System
Best order of raid lvm and luks
Encrypted Storage with LUKS, RAID and LVM2
© 2025 mgmsam.pro. Все права защищены.